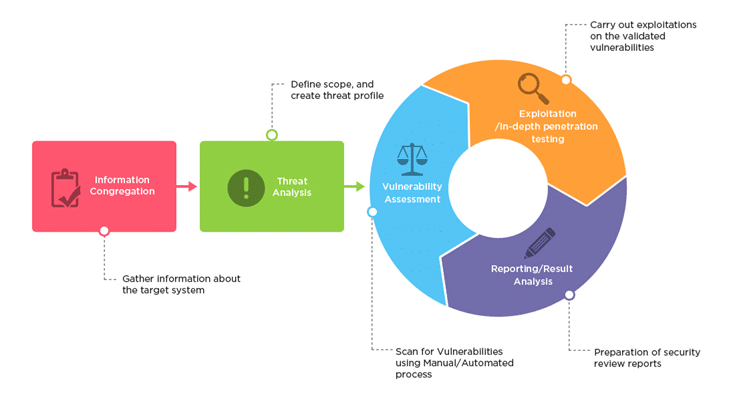
Aliz Infotech penetration test popularly known as pen-test will evaluate the security of an IT infrastructure by safely trying to exploit vulnerabilities. These vulnerabilities may exist in operating systems, services and application flaws, improper configurations or risky end-user behavior. Pen Test assessments are also useful in validating the efficacy of defensive mechanisms, as well as, end-user adherence to security policies.
Penetration tests are performed using manual or automated technologies to systematically compromise servers, endpoints, web applications, wireless networks, network devices, mobile devices and other potential points of exposure. At Aliz Infotech we access vulnerabilities in the system, our testers may attempt to use the compromised system to launch subsequent exploits at other internal resources by trying to incrementally achieve higher levels of security clearance and deeper access to electronic assets and information via privilege escalation.
Penetration testing will measure the feasibility of systems or end-user compromise and evaluate any related consequences such incidents may have on the involved resources or operations.